0
Windows users: Lost both Administrator user account name and password? Perhaps you need access without changing any existing administrative accounts? KON-Boot not doing it for you?
*** NOTE*** This post relates to bypassing Windows Operating System security.
The method discussed here is for HOME USE ONLY! It is NOT be used on systems that do not belong to you. Any problems arising from following this method are YOUR responsibility.
The beauty of this method is that it uses built in commands run from within the O/S you are gaining access to. This means that the likelihood of corrupt security databases / registries / etc are diminished to practically zero (there is always a chance of corruption: nothing is without risk!).
A similar exercise to this used to exist back in the NT4 days, but instead of targeting sticky keys executable, you targeted the NT4 default screeensaver.
This method works any version of Windows that ships with the Sticky Keys application. So that's Windows 95 and up.
How To (Short Version)
If you know what your doing and don't need a step by step, here's what to do in a nutshell:
- Boot from an alternative O/S and replace sethc.exe with cmd.exe
- Reboot target O/S and lauch stickykeys (press shift five times) to launch sethc.exe/cmd.exe
- Either:
- Use net localgroup Administrators to list existing local administrators and then net user USERNAME NEWPASSWORD to change the password of an existing administrative account
- Create new administrative account using: net user /add NEWUSER NEWPASSWORD and net localgroup Administrators /add NEWUSER to add new-user to the local administrators group
How To (Long Version with Screen Shots)
For the example process shown here, I'm going to access a Windows 7 installation. For my alternative operating system, I'm going to use Ubuntu Desktop 10.04.
OK Here's how.
- Grab yourself a copy of Ubuntu, Windows PE or Knoppix Doesn't matter which. The object here is to have an alternative method of booting the target system and gaining access to the drive containing the target Windows operating system.
- Create the alternative O/S boot CD/DVD or USB (for creation of an bootable Ubuntu USB, see my Unetbootin)
- Boot the alternative O/S.
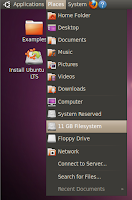
- Open Places Menu. Select Local Disk:
- Navigate to Windows\System32:
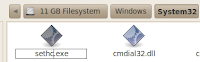
- Find the file sethc.exe, right click and rename to sethc.old:
- Find the file cmd.exe, right click and select Copy:
- Right Click again and select Paste:
- Find the file called cmd (copy).exe and rename this file to sethc.exe:
- Shutdown, remove Ubuntu CD/USB and reboot back into Windows
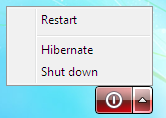
- At Windows logon prompt press shift key five times to launch stickykeys application sethc.exe (which we have replaced with cmd.exe):
- Once command prompt opens (dont worry about any message text error messages), create new administrative account using: net user /add NEWUSER NEWPASSWORD
- Enter net localgroup Administrators /add NEWUSER to add new-user to the local administrators group:
- If needs be, (to get the new user to appear on the login screen) restart windows:
- Login as the new user:
- CLEAN UP. Open C:\Windows\System32 and find sethc.exe:
- Delete sethc.exe:
- Find sethc.old, right click and select Copy. Right click again and Select Paste:
- Rename the file sethc - Copy.old to sethc.exe:
- Press shift five times to ensure that sticky keys launches OK:




























0Awesome Comments!